In today’s digital landscape, privileged identity management (PIM) has emerged as a critical pillar of cybersecurity, safeguarding organizations against the escalating threats posed by unauthorized access to sensitive data and systems. PIM empowers businesses to establish robust strategies for managing and controlling privileged accounts, minimizing risks and ensuring the integrity of their most valuable assets.
As organizations navigate the complexities of modern IT environments, the importance of PIM cannot be overstated. This comprehensive guide delves into the intricacies of PIM, providing a roadmap for implementing and managing effective solutions that protect your organization’s digital crown jewels.
Understanding Privileged Identity Management (PIM)
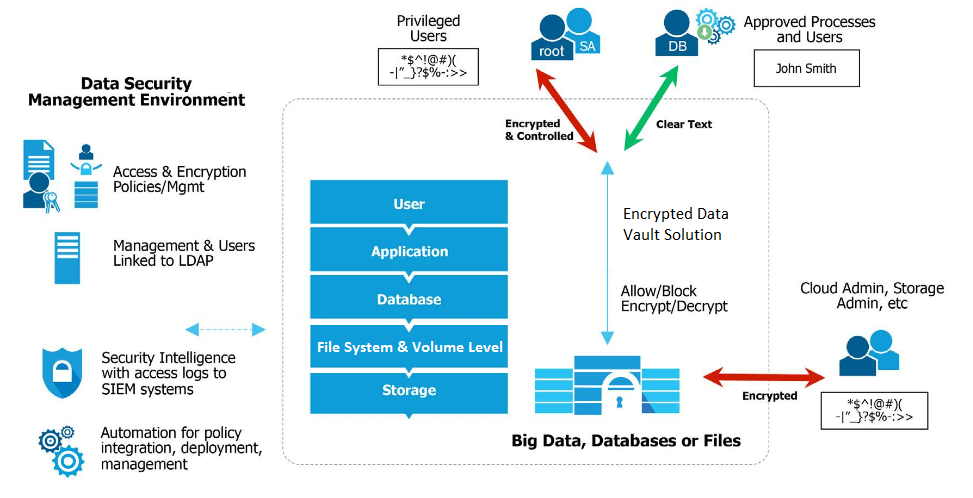
Privileged Identity Management (PIM) is a crucial aspect of modern cybersecurity strategies. It focuses on securing and managing privileged accounts, which are highly powerful accounts with elevated permissions to access critical systems, data, and applications within an organization.
PIM helps organizations prevent unauthorized access, data breaches, and system disruptions by implementing robust controls and processes for managing privileged accounts. It ensures that only authorized individuals have access to privileged accounts and that their activities are monitored and audited.
Types of Privileged Accounts
There are various types of privileged accounts, each with its own level of access and potential risks:
- System administratorshave full control over operating systems, including the ability to create, modify, and delete user accounts, install software, and configure security settings.
- Database administratorshave access to sensitive data stored in databases, including customer information, financial data, and intellectual property.
- Application administratorshave the ability to manage and configure specific applications, including web servers, email systems, and enterprise resource planning (ERP) systems.
li> Cloud administratorshave access to cloud computing platforms, such as Amazon Web Services (AWS) and Microsoft Azure, and can manage virtual machines, storage, and networking resources.
Key Components of a PIM Solution
A comprehensive Privileged Identity Management (PIM) solution encompasses several essential components that work together to effectively manage and secure privileged accounts. These components include:
Identity Governance and Administration (IGA)
IGA provides centralized control over the creation, modification, and deletion of privileged accounts. It enforces access policies, automates provisioning and deprovisioning processes, and ensures compliance with regulatory requirements.
Password Management
Password management solutions securely store and manage privileged passwords, preventing unauthorized access and ensuring compliance with password security best practices. They support features such as password rotation, encryption, and multi-factor authentication.
Privileged identity management is a critical aspect of securing your organization’s data and resources. To effectively manage privileged identities, organizations should consider implementing a practice management institute. The practice management institute provides a comprehensive approach to managing privileged identities, including identity lifecycle management, access control, and auditing.
By implementing a practice management institute, organizations can enhance their privileged identity management practices, reduce the risk of security breaches, and improve overall data security.
Session Management
Session management tools monitor and control privileged user sessions. They provide real-time visibility into user activities, enforce session timeouts, and terminate sessions when necessary to mitigate the risk of unauthorized access.
Privilege Elevation Management, Privileged identity management
Privilege elevation management solutions control the elevation of user privileges to perform specific tasks. They enforce least privilege principles, ensuring that users only have the minimum level of access required to complete their job functions.
Monitoring and Auditing
Monitoring and auditing capabilities provide visibility into privileged user activities. They track and record all privileged access attempts, allowing organizations to detect suspicious behavior, investigate security incidents, and maintain compliance.
Implementing and Managing PIM
Effective implementation and management of a PIM solution is crucial for enhancing cybersecurity posture and minimizing the risks associated with privileged accounts. A well-structured plan and a comprehensive approach to managing privileged access are essential for successful PIM implementation.
Implementing a PIM solution involves several key steps:
- Assessment:Conduct a thorough assessment of the organization’s current privileged access landscape, identifying critical assets, sensitive data, and potential vulnerabilities.
- Planning:Develop a comprehensive plan outlining the PIM implementation strategy, including timelines, resource allocation, and stakeholder involvement.
- Selection:Evaluate and select a PIM solution that aligns with the organization’s specific requirements, considering factors such as functionality, scalability, and ease of use.
- Deployment:Implement the PIM solution according to the plan, ensuring proper configuration and integration with existing systems.
- Monitoring and Auditing:Establish ongoing monitoring and auditing mechanisms to track privileged access activities, detect anomalies, and ensure compliance.
Methods for Managing Privileged Accounts
Various methods can be employed for managing privileged accounts. Each method offers unique advantages and drawbacks, and the optimal choice depends on the organization’s specific needs and risk tolerance.
| Method | Description |
|---|---|
| Just-in-Time (JIT) Provisioning | Grants privileged access only when required, limiting the duration and scope of elevated permissions. |
| Least Privilege | Assigns the minimum level of privileges necessary to perform job functions, reducing the potential impact of account compromise. |
| Shared Accounts | Uses a single account for multiple users, but requires careful management and monitoring to prevent unauthorized access. |
| Role-Based Access Control (RBAC) | Defines roles with specific privileges and assigns them to users based on their responsibilities, simplifying management and reducing the risk of unauthorized access. |
| Two-Factor Authentication (2FA) | Requires users to provide two forms of identification, such as a password and a one-time code, to access privileged accounts. |
Importance of Monitoring and Auditing Privileged Access
Monitoring and auditing privileged access are critical for maintaining the effectiveness of PIM solutions. Regular monitoring helps detect suspicious activities, such as unauthorized access attempts or privilege escalation, enabling prompt response and mitigation.
Auditing provides a comprehensive record of privileged access activities, which can be used for compliance purposes, forensic investigations, and identifying trends or patterns that may indicate potential security risks.
Potential Risks and Mitigation Strategies Associated with PIM
- Insider Threats:Malicious or compromised insiders can leverage privileged access to compromise systems and data. Implement strong identity verification measures, enforce separation of duties, and conduct regular background checks to mitigate this risk.
- External Attacks:Hackers may target privileged accounts to gain access to sensitive information or disrupt operations. Implement strong authentication mechanisms, such as multi-factor authentication, and regularly patch and update systems to mitigate this risk.
- Configuration Errors:Incorrectly configured PIM solutions can create vulnerabilities. Conduct thorough testing and validation during implementation, and establish regular reviews to ensure ongoing compliance.
- Compliance Violations:Failure to comply with industry regulations or internal policies can result in penalties or reputational damage. Ensure the PIM solution aligns with relevant compliance requirements and conduct regular audits to verify adherence.
Final Conclusion
By embracing a proactive approach to PIM, organizations can proactively mitigate risks, strengthen their security posture, and empower their workforce to operate efficiently within a secure and compliant environment. The insights and strategies Artikeld in this guide serve as a valuable resource for organizations seeking to safeguard their privileged identities and ensure the integrity of their most critical assets.
Questions Often Asked: Privileged Identity Management
What are the key components of a PIM solution?
Essential components of a PIM solution include centralized management, access control, session monitoring, auditing, and reporting.
How can organizations implement a PIM solution effectively?
Effective PIM implementation involves planning, risk assessment, tool selection, policy enforcement, and ongoing monitoring.
What are the potential risks associated with PIM?
Potential risks include privilege escalation, lateral movement, data breaches, and compliance violations.
